Auth Social (OAuth)
A secure, full-stack OAuth authentication component with GitHub integration, server actions, and seamless user management for Next.js applications.
Social OAuth Authentication
A comprehensive OAuth authentication component that provides secure GitHub integration with beautiful UI, automatic user management, and seamless Next.js server actions integration. Features real-time feedback, secure token handling, and production-ready OAuth flow implementation.
Installation
Install the component using the AxionsJS CLI:
Configure your environment variables in .env:
Set up GitHub OAuth App in your GitHub Settings:
- Go to Settings → Developer settings → OAuth Apps
- Create new OAuth App
- Set Authorization callback URL to:
http://localhost:3000/api/auth/callback/github
Set up Prisma schema and push to database:
The component includes complete database models for users and OAuth accounts. Server actions and OAuth utilities are pre-configured and ready to use.
Database Schema
Add the following models to your schema.prisma file:
Run npx prisma db push after adding the schema to apply changes to your database.
Usage
Import and use the OAuthLogin component:
Component Props
| Prop | Type | Default |
|---|---|---|
onSuccess | (provider: string, user: any) => void | undefined |
onError | (error: string) => void | undefined |
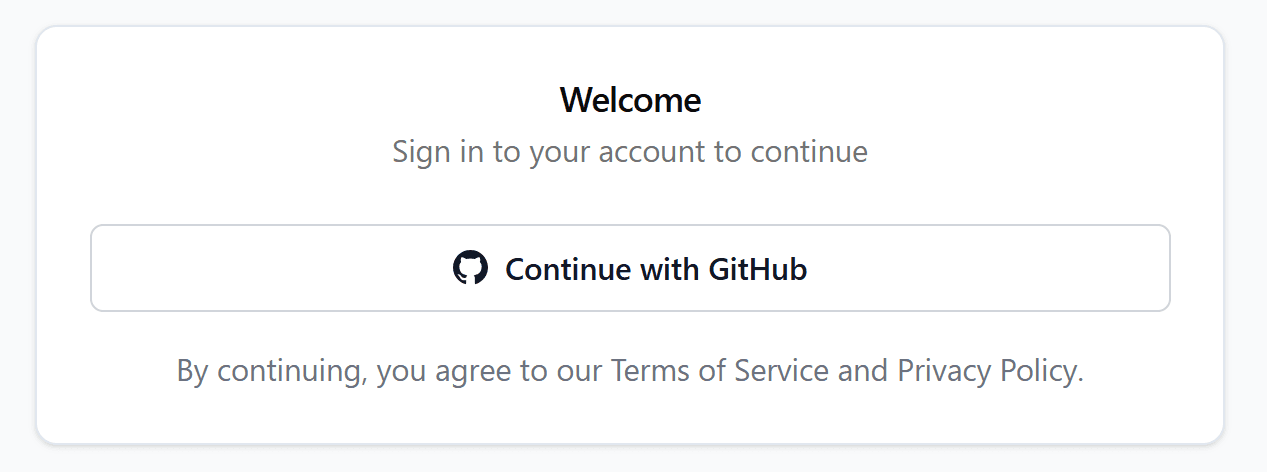
title | string | "Welcome" |
description | string | "Sign in to your account to continue" |
className | string | "" |
redirectUrl | string | undefined |
providers | "github"[] | ["github"] |
Server Actions
The component utilizes Next.js server actions for secure OAuth operations:
Features:
- Provider validation and configuration checking
- Secure URL generation with CSRF protection
- Comprehensive error handling
- Environment variable validation
Key Features
GitHub Integration
Complete GitHub OAuth flow with user profile and email access
User Management
Automatic user creation, account linking, and profile updates
Security First
CSRF protection, secure token handling, and environment validation
Error Handling
Comprehensive error states with user-friendly messaging
Loading States
Beautiful loading indicators and transition states
Type Safety
Full TypeScript support with proper type definitions
OAuth Utilities
The component includes utility functions for OAuth URL generation:
Utility Features:
- Secure URL generation with proper encoding
- CSRF protection with random state parameter
- Configurable redirect URLs
- Environment-based configuration
The OAuth utilities automatically handle scope configuration and security parameters for each provider.
Security Features
The Social Auth component implements multiple security layers:
- CSRF Protection: Random state parameter prevents cross-site request forgery
- Environment Validation: Checks for required OAuth credentials
- Secure Token Exchange: Direct server-to-server communication with OAuth providers
- Account Linking: Prevents duplicate accounts and manages user relationships
- Input Validation: Validates all OAuth responses and user data
- Error Handling: Secure error messages that don’t leak sensitive information
Always use HTTPS in production and keep your OAuth client secrets secure. Never expose client secrets in client-side code.
Conclusion
The Social Auth component provides a complete, production-ready solution for adding OAuth authentication to your Next.js applications. With GitHub integration, comprehensive security features, and seamless server actions integration, it delivers both excellent user experience and robust authentication capabilities.